Hacked by – WordPress Rest API Vulnerability in the Wild(v. 4.7-4.7.1)
As WordPress continues to grow in popularity, so does the complexity of this open source CMS. WordPress has come a long way from its early days in 2003 as a basic blogging platform and has become the most popular online publishing platform in the world.
Your website is a valuable business research, and just like in real-life there are individuals out there who want to take advantage of opportunities to benefit at the expense of others. If you own a website built in WordPress, then you know the ease and accessibility the open source CMS offers. However, the continued additions to WordPress can leave ways that hackers can use to access your website without your authorization.
The API Rest Vulnerability Found In The Wild
The most recent exploit was discovered on January 20, 2017, by WordPress security firm Sucuri. Marc-Alexandre Montpas, a security analyst at Sucuri, was the first to find the vulnerability during routine checks of open source projects. After discovering this vulnerability, Montpas promptly notified the WordPress security team and passed along his findings.
Upon their notification, WordPress contacted various companies to help protect users while they developed a fix for the REST (Representational State Transfer) API vulnerability. The WordPress security team worked diligently to create a fix for this vulnerability, and within only six days WordPress released a patch for the vulnerability on January 26, 2107, and disclosed their findings to the public.
WordPress Hacked?
If your WordPress Website has been hacked then we can help you with our WordPress Hacked Fix Services, where we can clean and update your site in 24 hours or even less. We also offer a 30 days period where you will get free cleaning services in case you WordPress website gets hacked again.
How Does A Hacker Exploit the REST API Vulnerability?
The WordPress REST API was introduced in the core code of WordPress and enabled by default in version 4.7.0. This API allows different computer programs to access your website to update, create, and delete WordPress posts. For example, if you website wants to display specific content based on the location of your visitor, then the REST API makes it easy to show this dynamic content.
Since the REST API looks for individually crafted HTTP requests to specific URLs, anyone can ask the public URL from any website. Through some basic manipulation, anyone visiting your site can potentially gain direct access to your posts on your site.
If someone knows how to fool the gatekeeper that WordPress uses to discern user credentials, then they will be able to alter content on your website.
What’s The Risk Of This Exploit For Your Business?
While the vulnerability has been public for less than a week, thousands of WordPress websites have fallen victim to the exploits of several malicious groups.
These groups alter content on vulnerable sites as a way to brag about their abilities, but others take advantage of the vulnerability to benefit their interests. The main types of exploits hackers have implemented in the wild so far are defacement campaigns, SEO spam and crimeware injections.
Defacement Campaigns
Some hacking groups have used this vulnerability to deface companies. While not irreversible or a business-ending hack, victims will find their SERPs displaying headlines and other content displaying different information than intended. If your website is hijacked and falls victim to this exploit, then you will be showcasing messages not approved by your brand.
Defacement campaigns are some of the easiest attacks hackers can perform on a vulnerable website. Just changing a few settings on the meta information of pages, they can change the SERP for your site.
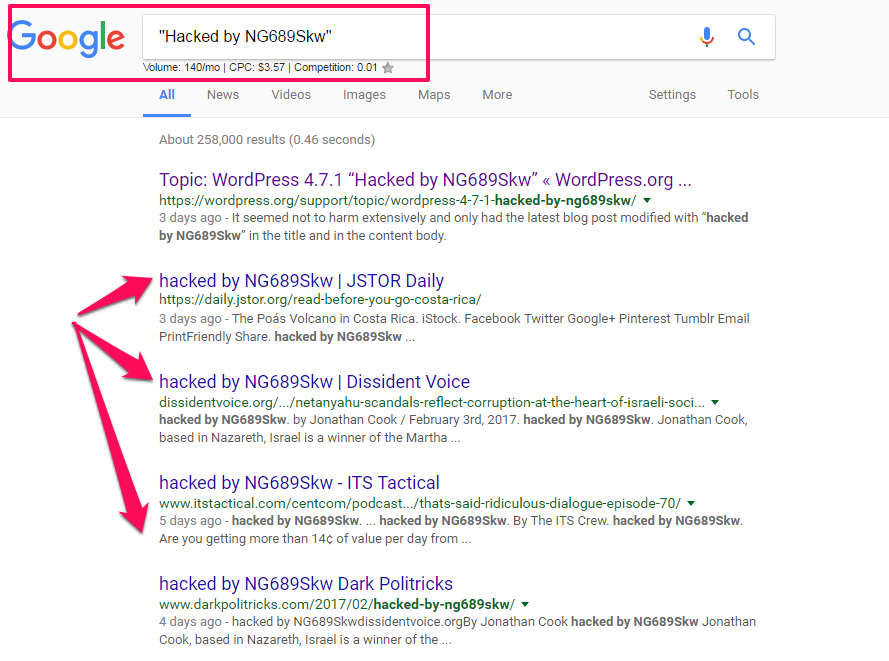
SEO Spam Exploitations
Defacement campaigns are not the only way hackers are exploiting the vulnerability. Savvy attacks also include manipulating site content to serve the SEO interests of unauthorized users.
Also known as "spamdexing", SEO Spam is the practice of creating websites or online content that will rank high in search engines through illegitimate strategies.
Since the REST API vulnerability allows hackers to access vulnerable sites, malicious groups have the ability to inject new content into pages and images on your website. This new, unapproved content could not only serve their interests, but this type of attack will also hurt your brand.
While defacing campaigns could hurt your online reputation, SEO spam exploitation could become the prominent way that hackers abuse the vulnerability for monetary interests. The reason SEO spam will be the most popular exploit is that hackers can use vulnerable websites to boost their online rankings with backlinks and other SEO practices.
Other Content Injection Attacks
While having your SERPs altered or SEO spam could hurt your business, there are other more severe content injection attacks that hackers can perform on your site using this vulnerability. The most concerning content injection attack that a hacker could perform on your website deal with placing the code on your site that would cause your visitors to download harmful content.
Once a hacker gains access to your website using the REST API vulnerability, they could add malicious content to your pages. In some instances, this content can install crimeware on a user’s computer by using pre-existing web browser vulnerabilities.
After this code is executed and fitted to a computer the user could be asked to download and install software that contains malicious programs. This means that if your website is not updated, a hacker can use your site as a tool to harm your visitors all without your knowledge.
Protecting Your WordPress Website
We suggest that site owners take basic precautions to protect their site. While the first defacement campaigns were seen 24 hours after the vulnerability was made public, the increased frequency of instances appearing is startling. So, what should you do if you find yourself a victim of these malicious attacks?
- Make a complete backup of your database and files for your website. Move these files to a safe location, so you always have something to reference moving forward.
- Update your WordPress version to 4.7.2.
- Locate and restore the most recent backup files you have before the attack.
- Login to /wp-admin/ to check that the files are clean and synchronize to the current WordPress version.
- Audit your website to ensure that all files are clean of the exploit and your content is as it was before the hack.
- Consider using cloud-based web application firewalls (WAF) to prevent these types of attacks in the future.
The most efficient solution to protect your WordPress site is also the easiest. The best way to harden your WordPress installation is to keep your WordPress version and plugins updated at all time.
What To Do If Your WordPress Website Is Hacked
Keeping your site and plugins updated can take a lot of time and energy, and sometimes you can easily forget to update your website. Unfortunately, there are individuals out there who will exploit your business for their gains. The most recent REST API vulnerability shows how easy it is for unauthorized users to take advantage of honest, hardworking business owners like yourself.
It can be overwhelming and stressful if your website is hacked. No one likes the feeling of being a victim, and you have worked too hard to help out dishonest folks. Instead of worrying about the technical side of things, you can trust the years and experience of FixMyWP to clean your WordPress and get your business back on track.

