The Definitive Guide about Backdoor Attacks – What is a backdoor
This will be a series of 4 guides in which we are going to try and show how backdoor attacks work and how they can be prevented. These security guides will be a bit more advanced than usual but I assure you it will worth the extra time you may need to read them and understand them.
A backdoor is a method that allows the bypass of some or all security checks in order to control some aspect of a system or an application. A backdoor may take the form of a separate program, a hidden piece of code or a hardware feature. In this series of articles we will talk about different types of backdoors, how they work, and how to defend yourself against them.
Why they are dangerous
If a hacker has a backdoor to your web server, the server may be abused without your knowledge. There can be a number of reasons for a hacker to have a backdoor in a system, here are three of them:
Distributed Denial of Service (DDoS)
The first one is when a hacker forces the affected server to participate in a Distributed Denial of Service Attack. This happens by making the server send lots of packets to a certain destination.
Denial of service attack occurs when a hacker tries to make a machine or network resource unavailable, for example, by overwhelming the resource with a large amount of traffic. The denial of service becomes distributed when multiple machines all over the world participate in the same attack. In this case, the hacker will have backdoors in a lot of systems that can all be used to perform a distributed denial of service attack. The servers which participate in such attacks might eventually be blacklisted.
Distribute malware
Another reason the hacker might set up a backdoor in your webserver, is to distribute malware to the website’s visitors. This malware is usually ransomware or adware wherein the hacker will benefit financially from distributing it.
When this occurs, the site will become blacklisted by browsers like Chrome.
Steal information
In this case, the backdoor will be a way for the hacker to access the webserver from time to time to steal important information from the server, like customer data or to use the server as a pivoting point to steal from an adjacent network. The hacker usually tries to be as stealthy as possible by not making any noise or affecting the service. In fact, you might not notice anything wrong with your server at all. Discovering such backdoors are difficult, not only because they may use advanced techniques, but because you might not even know they are there. One way to discover such a backdoor is by periodically checking the appropriate logs. In addition, securing the server is the best way to prevent such things from happening.
Backdoor types
Backdoors can be categorized using multiple criteria. Web shell backdoors and system backdoors are the two types that will be discussed in this article.
Web Shell backdoor
Web shell backdoor is simply having a backdoor using a web shell. So, what is a web shell?
A Web shell is a type of command-based web page (script), that enables remote administration of the machine. In the next article about Backdoor Attacks we will talk more in depth about web shell backdoors.
System backdoor
System backdoors are some of the most popular types of backdoors. They are also the main target for hackers because system backdoors give them more flexibility and stability comparing to web shell backdoors. System backdoors can vary a lot, depending on the situation, but most of the time they consist of a program that connects back to the hacker waiting for commands from him to execute. We will talk more about this topic in the upcoming articles.
Backdoor examples
Developer's backdoors
What? Yes, you heard it right. The website developers might create backdoors in their own code. Even though this is supposedly done for a good purpose we strongly disagree with any external access to a site without having the site owner approval and prior knowledge. Usually developers create a backdoor for themselves in the code while testing a specific feature that otherwise will take longer time testing with the normal security checks. An example of a developer backdoor is in the following picture:
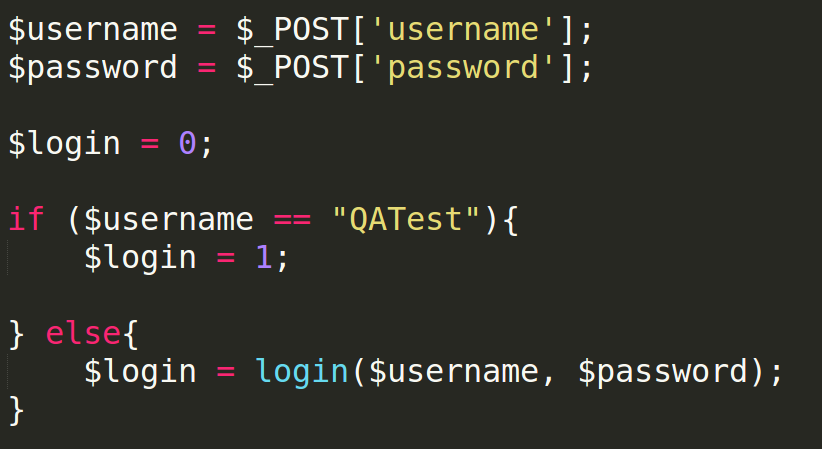
What the code above means is that, the username and password will be checked using the function login(), and unless the username is "QATest" access will be granted regardless of the password.
These types of backdoors are hard to detect, and easy to forget. The developer has to make sure that the application doesn't go to production with these types of backdoors because hackers might use them to their advantage.
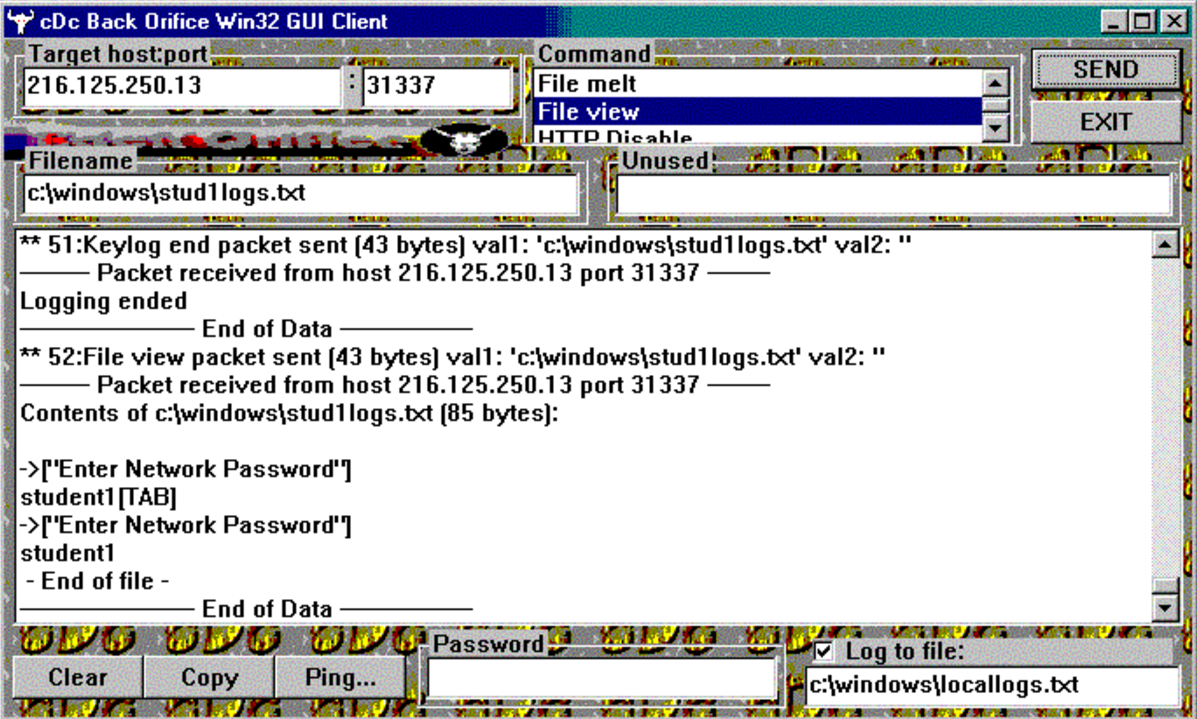
Back Orifice
Back Orifice was created in 1998, developed by Sir Dystic, and considered to be the first backdoor. It allowed computers running Windows to be controlled remotely by the hacker. The backdoor was created to demonstrate the lack of security in Windows’ systems back then.
Pirated commercial WordPress plugins
Some pirated commercial WordPress plugins found on the Internet contain backdoors. Some of them use advanced obfuscation techniques to hide, so it is difficult to be spotted by a normal user. That being said, the best way to avoid this type of backdoor is to not use pirated plugins as they might use your website to distribute malware.
In our next Definite Guide about Backdoor Attacks article, we will talk about webshell based backdoors, how they work, how to create one, how to protect yourself against them, and more.